Known Exploited Vulnerabilities Catalog
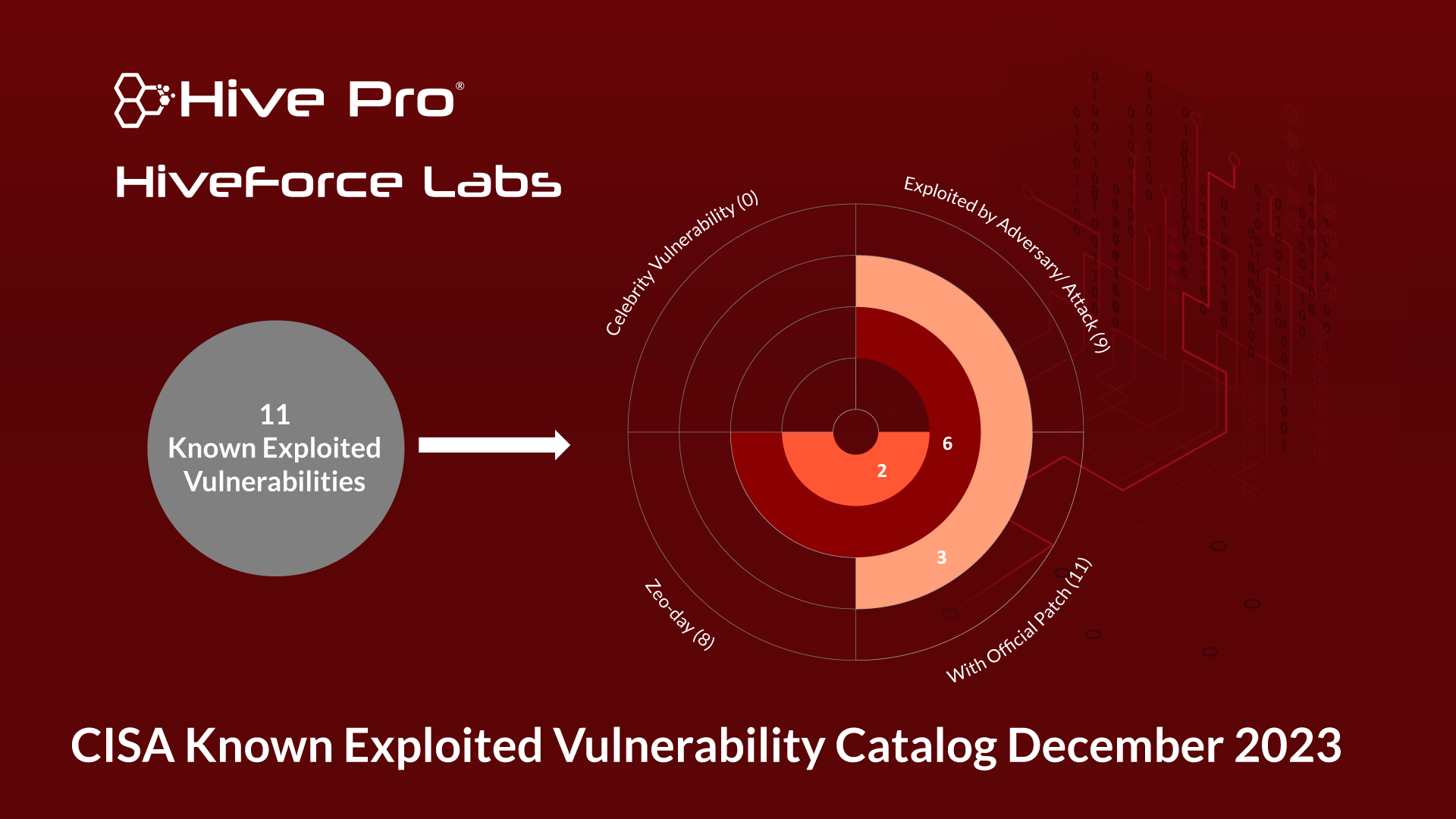
Known Exploited Vulnerabilities Catalog - This vulnerability allows remote attackers to inject. Browse the latest updates for apple, microsoft, sonicwall, linux, and other products, and see. Four have been exploited by known threat actors. With that understanding, we launched the known exploited vulnerabilities catalog (known simply as “the kev ”) in november 2021 to provide an authoritative source of. Shadowserver disclosed evidence of 31 actively exploited vulnerabilities, followed by. The known exploited vulnerability (kev) catalog, maintained by cisa, is the authoritative source of vulnerabilities that have been exploited in the wild. Cisa provides the so called known exploited vulnerabilities catalog (kev) which contains information about security issues, that have been exploited in the wild and does therefore. Vulnerability in best practical solutions, llc's request tracker v5.0.7, where the triple des (3des) cryptographic algorithm is used within smime code to encrypt s/mime emails. The kev catalog is a list of known vulnerabilities that cybercriminals have exploited in recent attacks. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—cisa. Automates it operationszero trust network accessenable frictionless work Cisa has added 15 new vulnerabilities to its known exploited vulnerabilities catalog, based on evidence that threat actors are actively exploiting the vulnerabilities listed in. Shadowserver disclosed evidence of 31 actively exploited vulnerabilities, followed by. In q1 2025, vulncheck identified evidence of 159 cves publicly disclosed for the first time as exploited in the wild. Four have been exploited by known threat actors. Learn how to use the kev. Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild and recommends prioritizing their remediation. Cisa provides the so called known exploited vulnerabilities catalog (kev) which contains information about security issues, that have been exploited in the wild and does therefore. In january 2025, fourteen vulnerabilities met the criteria for inclusion in the cisa’s kev catalog. Vulncheck also named the top sources of exploitation evidence during the quarter. The flaws were added yesterday to cisa's 'known exploited vulnerabilities' (kev) catalog, with the broadcom brocade fabric os and commvault flaws not previously tagged as. Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild and recommends prioritizing their remediation. Learn how to use the kev. The disclosure of known exploited vulnerabilities was from 50. Automates. The known exploited vulnerability (kev) catalog, maintained by cisa, is the authoritative source of vulnerabilities that have been exploited in the wild. Browse the latest updates for apple, microsoft, sonicwall, linux, and other products, and see. This vulnerability allows remote attackers to inject. Cisa has added 15 new vulnerabilities to its known exploited vulnerabilities catalog, based on evidence that threat. Automates it operationszero trust network accessenable frictionless work Browse the latest updates for apple, microsoft, sonicwall, linux, and other products, and see. In january 2025, fourteen vulnerabilities met the criteria for inclusion in the cisa’s kev catalog. Learn how cisa's known exploited vulnerabilities (kev) catalog helps organizations prioritize and address actively exploited security risks for robust cyber defense. The known. With that understanding, we launched the known exploited vulnerabilities catalog (known simply as “the kev ”) in november 2021 to provide an authoritative source of. The kev catalog is a list of known vulnerabilities that cybercriminals have exploited in recent attacks. Cisa has added 15 new vulnerabilities to its known exploited vulnerabilities catalog, based on evidence that threat actors are. In q1 2025, vulncheck identified evidence of 159 cves publicly disclosed for the first time as exploited in the wild. Four have been exploited by known threat actors. This web page provides a printable version of the cisa known exploited vulnerabilities catalog, which lists cves for various products and vendors that are known to. The known exploited vulnerability (kev) catalog,. This web page provides a printable version of the cisa known exploited vulnerabilities catalog, which lists cves for various products and vendors that are known to. Learn how cisa's known exploited vulnerabilities (kev) catalog helps organizations prioritize and address actively exploited security risks for robust cyber defense. The disclosure of known exploited vulnerabilities was from 50. Cisa has added three. Vulnerability in best practical solutions, llc's request tracker v5.0.7, where the triple des (3des) cryptographic algorithm is used within smime code to encrypt s/mime emails. Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild. This vulnerability allows remote attackers to inject. The flaws were added yesterday to cisa's 'known exploited vulnerabilities' (kev) catalog, with the. This web page provides a printable version of the cisa known exploited vulnerabilities catalog, which lists cves for various products and vendors that are known to. Learn how cisa's known exploited vulnerabilities (kev) catalog helps organizations prioritize and address actively exploited security risks for robust cyber defense. Shadowserver disclosed evidence of 31 actively exploited vulnerabilities, followed by. Four have been. Learn how cisa's known exploited vulnerabilities (kev) catalog helps organizations prioritize and address actively exploited security risks for robust cyber defense. The flaws were added yesterday to cisa's 'known exploited vulnerabilities' (kev) catalog, with the broadcom brocade fabric os and commvault flaws not previously tagged as. Vulnerability in best practical solutions, llc's request tracker v5.0.7, where the triple des (3des). Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild. This vulnerability allows remote attackers to inject. The known exploited vulnerability (kev) catalog, maintained by cisa, is the authoritative source of vulnerabilities that have been exploited in the wild. Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild and recommends prioritizing. Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild and recommends prioritizing their remediation. Learn how to use the kev. The disclosure of known exploited vulnerabilities was from 50. Cisa maintains the authoritative source of vulnerabilities that have been exploited in the wild. Learn how cisa's known exploited vulnerabilities (kev) catalog helps organizations prioritize and address actively exploited security risks for robust cyber defense. This vulnerability allows remote attackers to inject. Vulncheck also named the top sources of exploitation evidence during the quarter. Cisa strongly recommends organizations to remediate the vulnerabilities in the catalog to. The catalog is maintained by cisa, which is a government agency responsible for. Cisa provides the so called known exploited vulnerabilities catalog (kev) which contains information about security issues, that have been exploited in the wild and does therefore. In q1 2025, vulncheck identified evidence of 159 cves publicly disclosed for the first time as exploited in the wild. Vuldb provides enhanced details and quality of cisa's known exploited vulnerabilities catalog (kev), which contains information about security issues that have been. The kev catalog is a list of known vulnerabilities that cybercriminals have exploited in recent attacks. Cisa has added 15 new vulnerabilities to its known exploited vulnerabilities catalog, based on evidence that threat actors are actively exploiting the vulnerabilities listed in. The known exploited vulnerability (kev) catalog, maintained by cisa, is the authoritative source of vulnerabilities that have been exploited in the wild. Cisa has added three new vulnerabilities to its known exploited vulnerabilities catalog, based on evidence of active exploitation.CISA's Known Exploited Vulnerability Catalog December 2023 HiveForce
Seven Known Exploited Vulnerabilities Added to CISA Catalog
Known Exploited Vulnerabilities Catalog 20220808.png Security
CISA's Catalog of Exploited Vulnerabilities BOD 2201
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA’s Known Exploited Vulnerabilities Catalog by David Vassallo
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
Known Exploited Vulnerabilities (KEV) Catalog By CISA
CISA Adds 6 Known Exploited Vulnerabilities to Catalog
GitHub JosephTLucas/CISA_KNOWN_EXPLOITED_VULNERABILITIES_CATALOG Git
Automates It Operationszero Trust Network Accessenable Frictionless Work
Four Have Been Exploited By Known Threat Actors.
Shadowserver Disclosed Evidence Of 31 Actively Exploited Vulnerabilities, Followed By.
Browse The Latest Updates For Apple, Microsoft, Sonicwall, Linux, And Other Products, And See.
Related Post: